I have figured it out, with the help of a chat guy. There are steps missing from the documentation about installing the SecureAccess app. In fact, none of the documentation on the iXpand drive contains anything about the installation of the secureaccess application on a Mac. Here's the crux of it. The app must be installed on the iXpand drive itself, not the Macintosh Hard Disk. Their instructions on accessing secure files on your Mac computer *start* with (to paraphrase) 'Launch the SecureAccess. App and click next'.
Jan 23, 2014 - Access to your private vault is protected by a personal password, and your files are automatically encrypted - so even if you share your SanDisk. Jun 4, 2016 - Greetings: I placed some files from work onto the Secure Access Vault on my 32GB SanDisk USB 3.0 in hopes of opening/transferring them to. Ms word office 2016 for mac locks up.
First, it doesn't say that that app *will be* located in the root directory of the iXpand drive and second, it completely skips the part about running the app's package installer and selecting the iXpand drive as the install destination. I don't think it's necessarily intuitive that the app's install location should be on the drive itself. In retrospect, that makes sense, but I'm a computer scientist, and *I* didn't intuitively get that at first. So I think that a novice user might get stuck there, thinking the app will not install. Why not have these details in the documentation? Besides that, another deficiency of the documentation is that they claim the only way to fix an iPad-unrecognized iXpand drive is using an iOS 8 device or a Windows computer (neither of which I have, BTW). Being a computer scientist, I had wanted to install my own encrypted disk image on the drive - ran into some issues - and had reformatted the drive using Apple Extended (journaled), which caused the drive to not be recognized by the iPad iXpand app.
(Besides, as I found out, the.dmg format file isn't usable on the iPad.) But according to the documentation, I was screwed - stuck with a USB dongle that wouldn't work on my iPad! Well, the documentation is defficient, because you can fix this issue on a Mac computer. You simply have to run Disk Utility and reformat the drive using MS-DOS FAT format. Please update the SanDisk documentation to reflect this fix. While I'm on a rant. I put a bunch of files in the vault from my computer in their own directory structure. I was shocked to find out that to access these files on the iPad, I had to *move* them out of my directory structure (and decrypt them) and put them unsecured on the iXpand drive.
Then my only option to re-secure the files was to put them in the secure vault's *root* directory! I couldn't put them back in the directory they came from! Don't get me wrong. I appreciate the ability to maintain secure files and swap them back and forth from the computer to the iPad. This is the only method to do this I'm aware of without going through the internet, so it is useful. But this interface has, in my opinion, quite a ways to go. And don't get me started on the mac application's interface.
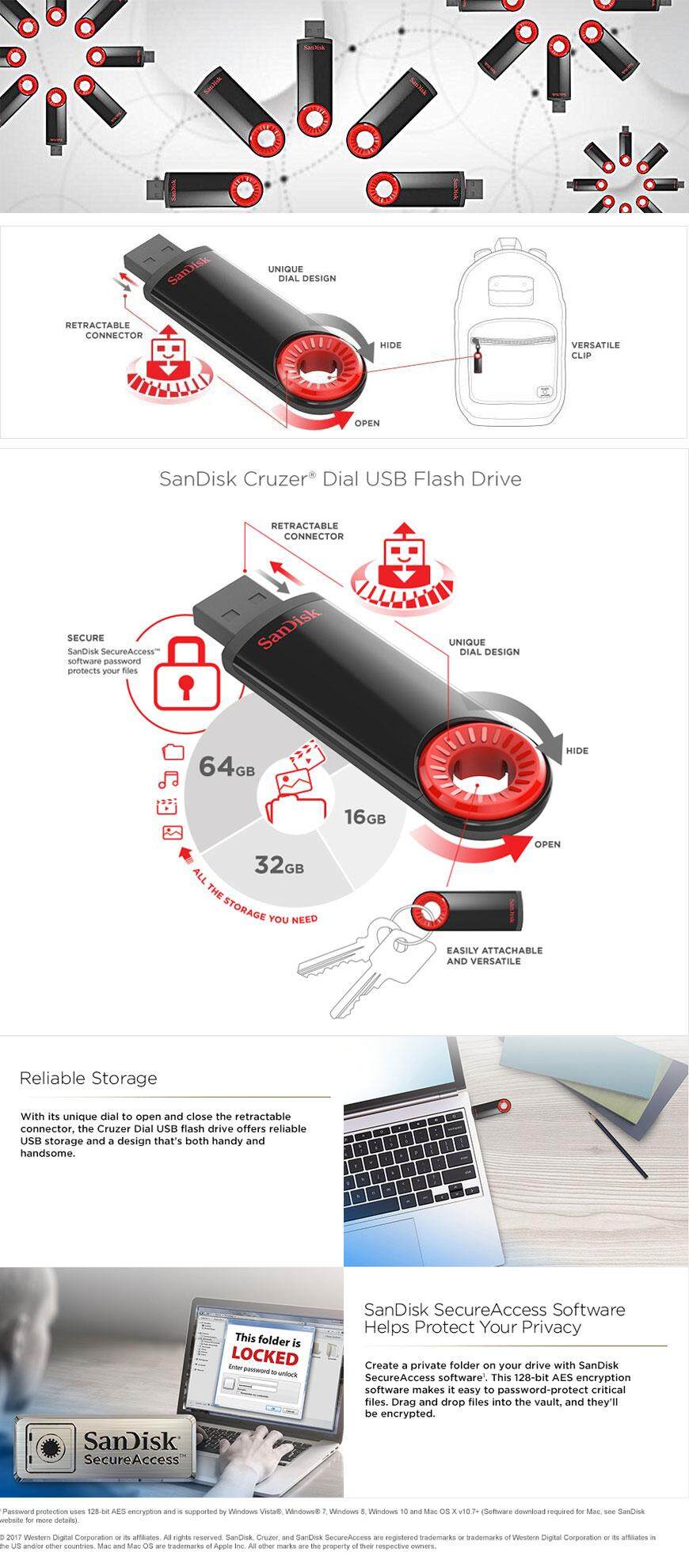
I haven't personally used it, so I can only guess based on the description. The usual issue with these tools is that you can only store/retrieve files in the 'vault', but not open them while inside. This is fine for securing files against loss of the stick, but forces you take them out of the vault to access them, thereby creating unencrypted copies each time. On the other hand they say a new 2.0 feature is 'Edit documents stored in “vault”', so maybe they found away around that, though any method that comes to mind either requires administrative privileges or is really hacky. 3d emulator mac. As for the security of the actual encryption, 128bit AES is perfectly secure, assuming it's used correctly. As it's a closed-source application and I can't find any info about their implementation, I really can't say anything about it. It's probably fine for general use as long as the NSA isn't after you, but if you have the option to install additional software I'd go with TrueCrypt.
: In, a one-time pad ( OTP) is an technique that cannot be if used correctly. In this technique, a is paired with random, secret (or pad). Then, each bit or character of the plaintext is encrypted by combining it with the corresponding bit or character from the pad using. If the key is truly, at least as long as the plaintext, never reused in whole or in part, and kept completely, the resulting will be impossible to decrypt or break. It has also been proven that any cipher with the perfect secrecy property must use keys with effectively the same requirements as OTP keys.
However, practical problems have prevented one-time pads from being widely used. Interesting: Parent commenter can. Will also delete on comment score of -1 or less. • • • • •.