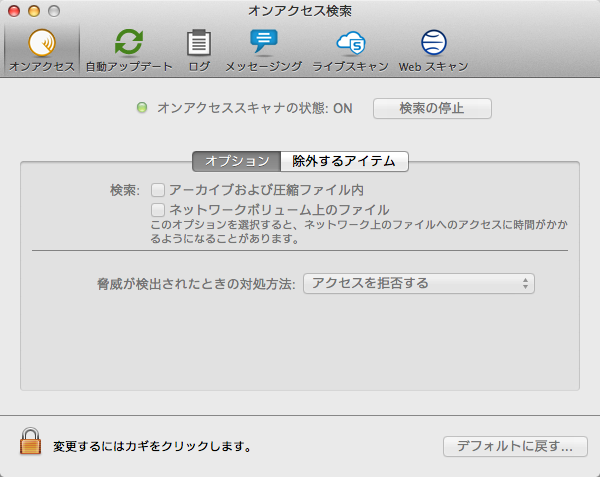
Sophos Home Premium offers Mac antivirus protection at a very reasonable price, but the absence of many advanced features found in the Windows edition is disappointing. Sophos is a big name in.
SHARE Endpoint security is still dominated by traditional anti-virus solutions, with Gartner ranking Symantec, Sophos, Trend Micro and Kaspersky as leaders in the field. But new next-generation endpoint security solutions are generating buzz as either replacements or supplements to existing security investments. These new solutions promise to stop zero-day attacks and, two big security threats that often slip by traditional anti-virus solutions. The endpoint security solutions featured here use a variety of emerging approaches and technologies. Quickbooks for mac update. In general, though, next-generation endpoint security relies on one of two methods to stop new attacks. Many use some form of advanced analytics -- whether from a pre-determined analysis of malware or by learning your network -- that monitors endpoint behavior and stops unusual events. Others leverage virtual sandboxes, whitelists or containers to ensure insecure endpoint activity remains cut off from the network.
To help cut through the hype, we've focused on how each endpoint security solution works and what's unique about the company. We've also identified whether the solution tries to replace or complement existing security tools.
You'll find information on which endpoint OSes each supports and whether the tool can provide security analytics. How it works: Bufferzone creates a virtual container around any applications you deem insecure. This can include browsers, email, Skype, FTP and removable storage devices.
Essentially, it segregates the corporate network into two zones: trusted and untrusted domains. The tool creates a virtual sandbox around the entire application environment, including related files, registries and network access that your administrator deems insecure. This allows the solution to contain malware, protecting not only your network but the rest of the end user's computer. What's unique: Bufferzone does not attempt to detect or block malware but instead focuses on containing all 'untrusted' sources. Onenote for mac upgrade changed position of tabs. Any infections are automatically confined to the container. The upside is it doesn't require maintenance of a blacklist or whitelist and, unlike traditional endpoint detection solutions, it doesn't need to learn to detect new, suspicious behaviors. 'It simply isolates threats like ransomware and zero-days so that they cannot do any harm,' the company notes.
Replace or complement: Bufferzone integrates existing SIEM solutions and Big Data analytics tools to identify targeted attacks. Supports: Windows devices Analytics: Bufferzone provides data to enterprise solutions that analyze endpoint data, such as Splunk and McAfee.
Big brag: Bufferzone is effective in blocking ransomware and preventing it from encrypting files on the endpoint or spreading to other computers on the network. It is fully integrated with McAfee ePO and with Landesk LDMS. Bonus points: • Transparency to end users and their applications • Scanning removable storage • A free home edition is available for download Barkly How it works: Barkly relies on proprietary behavioral analytics to detect techniques and behaviors common to all malware. An agent called Rapidvisor is installed locally on your endpoints and managed via a cloud-based portal. The agent watches in real-time across multiple levels of the system, including user space, operating system functions and CPU instructions.